
Every business faces the challenge of ensuring data security and maintaining safe operations. This has become even more challenging with the rise of work-from-anywhere (WFA) arrangements, which increases security risks. Besides securing WFA computers, other infrastructure elements—including on-premises network devices and phone systems—must be regularly updated and scanned. To build a strong foundation for your company’s security, it’s essential to understand and implement best practices for patch management.
Patch management program
Two fundamentals of information security practices are vulnerability management and patch management. While vulnerability management identifies cybersecurity risks, patching is infrastructure hygiene intended to cover known exploits. Ideally, both areas should work in tandem to identify and remediate vulnerabilities and help IT leaders allocate resources effectively.
It is imperative to establish ongoing vulnerability and patch management programs in your organization rather than treating it as a one-time or occasional activity. Ideally, monitoring vulnerabilities and patching should be carried out every month. Continuous assessment, preparation, deployment, and support processes are needed to ensure comprehensive coverage of all your operations.
To implement a comprehensive patch management program, there are several best practices to execute:
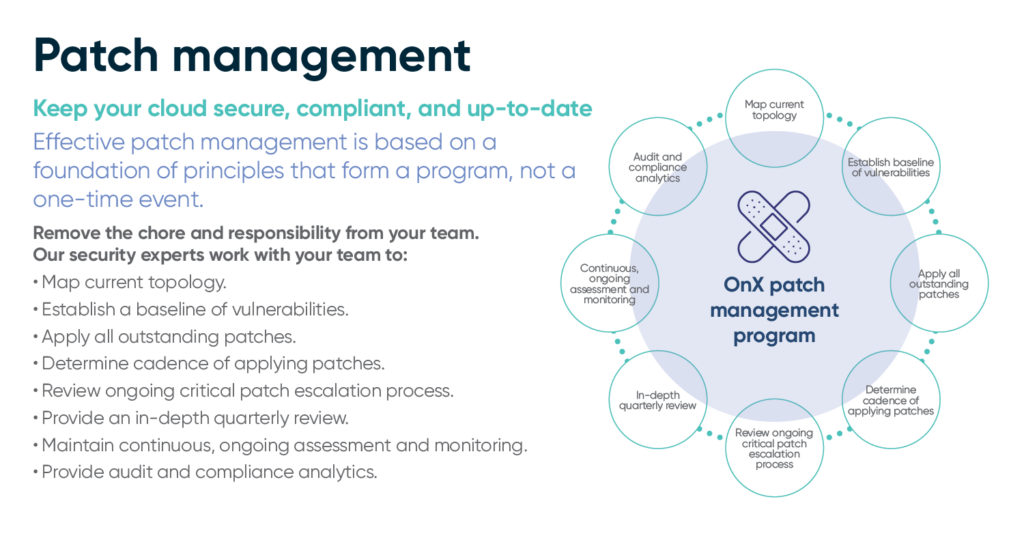
- Inventory of all applications and assets that need to be patched.
- Prioritize systems based on their risk level, focusing on the most critical ones first.
- Develop a patch management policy that outlines your approach.
- Back up your data to avoid loss in case of unexpected issues.
- Test and document all deployed patches in non-production environments to ensure they don’t cause any problems.
- Once you have tested and validated the patches, finalize their deployment in production in a phased rollout.
Learn more: I just met a vuln named Follina
Beginning the process
Keeping the above elements in mind, organizations that want to improve their patch management programs must carefully implement and maintain best practices over time. For busy IT teams, seeking the guidance of an experienced patch management provider like OnX Canada can be a valuable shortcut to establishing or revitalizing your patch management.
Catalog applications and digital assets
An audit of an enterprise’s hardware, software environment, and assets can help comprehend the risks, identify vulnerabilities, and prioritize patches. This inventory provides a comprehensive overview of existing systems and highlights the areas that require the most attention. It is crucial to update the “patch map” whenever new applications or infrastructure are incorporated into the organization’s technology stack. It is also vital to evaluate third-party application vendors and determine the vulnerabilities they may introduce into the environment.
Prioritize according to risk
Once your organization possesses an accurate and current understanding of its complete software and hardware infrastructure, it can assign appropriate levels of risk to each system or program. Address systems or programs with higher risk levels first. Furthermore, consolidating multiple versions of redundant software in your application portfolio can help reduce the risk of exposure.
Working with a managed services provider can help your team assess and prioritize your digital inventory while also implementing automation tools that can minimize manual tasks.
Patch prioritization is influenced by several factors, such as:
- Sensitivity of data.
- Importance to operations.
- Vulnerability level.
- Device group or operating system.
- Third-party vendors.
Learn more: Top five cybersecurity actions to take right now
Building patch management policies
Incorporating third-party software vendors into your patch management strategy is essential if your organization utilizes outside solutions. It is crucial to keep the third-party software up to date along with your proprietary software for your network environment to remain current. Updating third-party applications is necessary to address potential vulnerabilities.
Consider the following when setting up your patch management program policies:
- Cadence: Implement monthly updates for mission-critical patches with the same frequency for third-party vendors and as needed for urgent security vulnerabilities.
- Review: Conduct a quarterly review of patching procedures and issues.
- Monitoring: Monitor newly deployed patches and test to ensure successful application.
- Documentation: Maintain best practices with documentation such as a user testing log, backout procedures, or other checklist documentation.
Instituting backups before patch deployment
Applying new patches can be risky, even if you’ve tested them thoroughly. To mitigate these risks, it is critical to create full system backups of the assets before patching. This way, your team can revert to the working version if the patch causes problems.
Test patches in development environments
Testing patches in a non-production environment closely resembling your system is a vital best practice. Sandboxes should mimic your production environment as closely as possible by utilizing the same applications, hardware, and assets as much as possible. This helps identify and fix issues before rolling out patches to production.
Utilize a phased rollout
Prioritize caution over speed whenever possible. Implement the tested patch using a phased rollout, starting with the least critical production servers and moving to critical systems.
The patch management program in practice
Patch management service providers typically work on a 30-day timeline to keep systems current. They try to avoid disrupting services by scheduling patches after hours. Urgent security patches, so-called “out-of-band” releases, are an exception that may require faster implementation.
“Patch Tuesday” is the name Microsoft gives to the second Tuesday of every month when they release significant updates. Other companies have also followed this monthly cycle model, albeit some on different days. Examples include:
- During release week, patch specialists test patches on a non-production environment.
- Each patch is tested for at least 48 hours.
- Non-production patches deploy on Thursday or Friday.
- Production patches are installed the following week.
- Issues are closely monitored and remediated over the rest of the month.
- Reports are delivered to auditors and regulators to conclude the monthly cycle.
Watch: John Bruggeman and Jon Lloyd discuss more intelligent patching in this episode of Inside the CISO’s Office.
Full-spectrum cybersecurity
Outsourcing vulnerability and patch management services to OnX saves time and provides the following benefits:
- Thorough vulnerability assessments.
- 98% success rate in patching.
- Inventory, analysis, and prioritization of high-risk vectors.
- Expert guidance in patch management policy creation.
- 24x7x365 support.
OnX provides a comprehensive vulnerability assessment and patch management program that covers all aspects of your network environment, including endpoints, critical assets, equipment, and facilities. From planning and deployment to monitoring and auditing, our program ensures that your organization’s patch schedule is tailored to your needs. Our security team comprises highly skilled cybersecurity experts knowledgeable about the latest tools and processes and can guide your organization toward building a robust cyber defense.
Contact us today for more information on vulnerability assessment and patch management services.















